- Cisco Ios Download
- Cisco Ios 15 License Keygen Key
- Cisco Ios Version List
- Cisco Ios 15 License Key Generator
- Cisco Ios 15 License Keygen Free
After looking at the announcement for End of Life support for IOS 12.4 (and you know that IOS 15 is the next version dont you ?) it’s worth looking into the big changes in IOS Feature licensing in case you are not aware of them.
Single Image
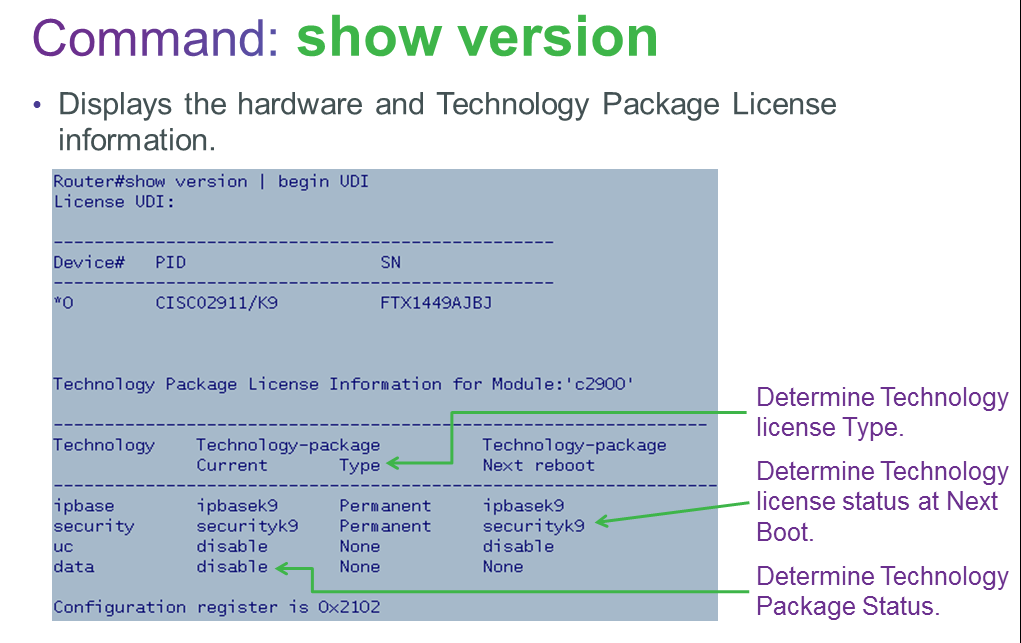
IOS 15 is a single software package for the hardware platform that your are using. Now that flash is cheap and large, there doesn’t need to be a different IOS image for the different versions with the advanced features. So you get one software image that has all the features for that platform.
Ipad2 Wifi Ios 5 serial: Cisco Ios 2009 keygen: Magic Ios 5.5 serials generator: Apple Ios 4.3.5 crack: Apple Ios 4.3.4 serial number maker: Cisco Ios Collection.iso serials key: Ios Sdk 4.0.1 keymaker: Cisco Ios Monster Collection 2008 keygen: Ios 4.1 serial keys gen: Iphone3gs Ios 5 serial key gen: Ios 4.2.1 keymaker: Lynda Com Ios 4 serial. Generate the license. After running this command, a file called iourc.txt will be created. Copy and paste the license key in the file to the Preference IOS on UNIX section of GNS3. IOS on UNIX section. Finally, everything is green😀!!!
Licensing and Cisco Licensing Manager
You should note that IOS 15 enforces licensing for the Advanced feature sets. That is, you will need to register a license key for every IOS image that needs Advanced IP and receive an activation key to activate those features.
Licensing is basically similar to how the ASA software licenses work today. You need to buy the license, receive the PAK key on a piece of paper, register this on Cisco website to receive an activation key and then enter it into the router. If you want access to the advanced feature sets, you will need to purchase the license and activate it on the router.
Yes, Cisco equipment just got a whole lot harder to manage.
Cisco License Manager
If you are a large company, it is time to implement Cisco Licensing Manager to manage the licenses on all of your equipment. This will allow you to manage and transfer licenses between physical units.
Operational Procedures
Note that when you replace a faulty router, you will have to activate the license on that router as part of the recovery process. So you will need to update your field engineers to make sure that they know how to do this and perform License Transfer Between Two Working Devices or get on the phone to the TAC or use the web to transfer a license.
I can’t see any point in blogging about this in detail, Cisco IOS 15.0 documentation is clear and concise as always. Cisco really does the best documentation.
You can find out more in the†Software Activation Configuration Guide.
Time to go and learn what you need to know.
Cisco Ios Download
Configure a certificate compatible with Cisco IOS by XCA on Ubuntu.
- Export a CA certificate in PEM-encoding on XCA:
 Click an image to zoom in.
Click an image to zoom in. Open the saved certificate file (TestCA.crt) by text editor.
-----BEGIN CERTIFICATE----- MIIDUjCCAjqgAwIBAgIBATANBgkqhkiG9w0BAQUFADBNMQswCQYDVQQGEwJKUDEO MAwGA1UECBMFVG9reW8xEDAOBgNVBAoTB2V4YW1wbGUxHDAaBgNVBAMTE2Npc2Nv .... aEXQ/TpHN3IQ5DwOakXFdbNgP1uP8IhvDLB7wnPY1cJpIFU4CB0= -----END CERTIFICATE----- |
- Generate RSA keys and create a Certificate Signing Request (CSR) on Cisco IOS (cisco1.example.com)
See Command References for Cisco IOS 15.1M&T for more details.

router(config)# show version .... Cisco IOS Software, 1841 Software (C1841-ADVSECURITYK9-M), Version 15.1(4)M8, RELEASE SOFTWARE (fc2) .... Cisco 1841 (revision 7.0) with 239616K/22528K bytes of memory. .... |
router(config)# hostname cisco1 cisco1(config)# ip domain example.com |
cisco1(config)# crypto key generate rsa modulus 2048 general-keys The key modulus size is 2048 bits Generating 2048 bit RSA keys, keys will be non-exportable...[OK] |
cisco1(config)# crypto pki trustpoint ciscoca cisco1(ca-trustpoint)# enrollment terminal cisco1(ca-trustpoint)# fqdn none cisco1(ca-trustpoint)# ip-address none cisco1(ca-trustpoint)# subject-name CN=cisco1.example.com,O=example,ST=Tokyo,C=JP cisco1(ca-trustpoint)# rsakeypair cisco1.example.com cisco1(ca-trustpoint)# revocation-check none cisco1(ca-trustpoint)# exit |
cisco1(config)# crypto pki authenticate ciscoca Enter the base 64 encoded CA certificate. End with a blank line or the word 'quit' on a line by itself (Paste the PEM-encoded contents of above TestCA.crt. The PEM header and footer are not included.) MIIDUjCCAjqgAwIBAgIBATANBgkqhkiG9w0BAQUFADBNMQswCQYDVQQGEwJKUDEO MAwGA1UECBMFVG9reW8xEDAOBgNVBAoTB2V4YW1wbGUxHDAaBgNVBAMTE2Npc2Nv .... aEXQ/TpHN3IQ5DwOakXFdbNgP1uP8IhvDLB7wnPY1cJpIFU4CB0= Do you accept this certificate? [yes/no]: yes Trustpoint CA certificate accepted. Certificate successfully imported cisco1(config)# exit cisco1# show crypto pki certificates ... CA Certificate Status: Available Certificate Serial Number (hex): 01 Certificate Usage: General Purpose Issuer: cn=testca.example.com o=example st=Tokyo c=JP Subject: cn=testca.example.com o=example st=Tokyo c=JP Validity Date: start date: xxxx end date: xxxx Associated Trustpoints: ciscoca Storage: nvram:ciscocaexamp#1CA.cer |
cisco1(config)# crypto pki enroll ciscoca Start certificate enrollment .. .... Include the router serial number in the subject name? [yes/no]: no .... Display Certificate Request to terminal? [yes/no]: yes Certificate Request follows: MIICsjCCAZoCAQAwTDELMAkGA1UEBhMCSlAxDjAMBgNVBAgTBVRva3lvMRAwDgYD VQQKEwdleGFtcGxlMRswGQYDVQQDExJjaXNjbzEuZXhhbXBsZS5jb20wggEiMA0G .... KKdrWOkisCNsOfivsOPXoA5Cw53aVQ |
Copy the displayed Certificate Request (CSR) contents (PEM), paste into a file by text editor and then save it as cisco1.example.com.csr.
Click an image to zoom in.
Cisco Ios 15 License Keygen Key
Before saving the file, you need to add the PEM header and footer like this:-----BEGIN CERTIFICATE REQUEST----- MIICsjCCAZoCAQAwTDELMAkGA1UEBhMCSlAxDjAMBgNVBAgTBVRva3lvMRAwDgYD
VQQKEwdleGFtcGxlMRswGQYDVQQDExJjaXNjbzEuZXhhbXBsZS5jb20wggEiMA0G
....
KKdrWOkisCNsOfivsOPXoA5Cw53aVQ
-----END CERTIFICATE REQUEST-----
Cisco Ios Version List
- Sign and export a new certificate for cisco1.example.com by XCA:
- Import the Certificate Signing Request (CSR) for cisco1.example.com.
- Sign a certificate for cisco1.example.com by TestCA.
- Export the certificate to a PEM file.
- File name: cisco1.example.com.crt - Open the signed certificate file (cisco1.example.com.crt) by text editor and copy the contents without the PEM header and footer.
Click an image to zoom in.
Click an image to zoom in.
Click an image to zoom in.
Cisco Ios 15 License Key Generator
- Import the signed certificate into Cisco IOS (cisco1.example.com)
Cisco Ios 15 License Keygen Free
cisco1(config)# crypto pki import ciscoca certificate Enter the base 64 encoded certificate. End with a blank line or the word 'quit' on a line by itself (Paste the certificate contents copied from the text editor above.) MIIDTzCCAjegAwIBAgIBAjANBgkqhkiG9w0BAQUFADBMMQswCQYDVQQGEwJKUDEO MAwGA1UECBMFVG9reW8xEDAOBgNVBAoTB2V4YW1wbGUxGzAZBgNVBAMTEnRlc3Rj .... pS/8x8Azvi9uXDp/Uv8FX5WtgmctUAqYlHogq9FN/PsSKNU= Router Certificate successfully imported |
cisco1# show crypto pki certificates Certificate Status: Available Certificate Serial Number (hex): 03 Certificate Usage: General Purpose Issuer: cn=testca.example.com o=example st=Tokyo c=JP Subject: Name: cisco1.example.com cn=cisco1.example.com o=example st=Tokyo c=JP Validity Date: start date: xxxxxx end date: xxxxxx Associated Trustpoints: ciscoca Storage: nvram:ciscocaexamp#2.cer CA Certificate Status: Available Certificate Serial Number (hex): 01 Certificate Usage: General Purpose Issuer: cn=ciscoca.example.com o=example st=Tokyo c=JP Subject: cn=ciscoca.example.com o=example st=Tokyo c=JP Validity Date: start date: xxxxxx end date: xxxxxx Associated Trustpoints: ciscoca Storage: nvram:ciscocaexamp#1CA.cer cisco1# show crypto pki trustpoints status Trustpoint ciscoca: Issuing CA certificate configured: Subject Name: cn=testca.example.com,o=example,st=Tokyo,c=JP Fingerprint MD5: xxxxxx AE222650 xxxxxx 3CE7EFFC Fingerprint SHA1: xxxxxx 88837420 xxxxxx 55B0EC8E xxxxxx Router General Purpose certificate configured: Subject Name: cn=cisco1.example.com,o=example,st=Tokyo,c=JP Fingerprint MD5: xxxxxx 1DC1EACB xxxxxx 8C16CA3E Fingerprint SHA1: xxxxxx 3C2DBF77 xxxxxx D35604A3 xxxxxx State: Keys generated ............. Yes (General Purpose, non-exportable) Issuing CA authenticated ....... Yes Certificate request(s) ..... Yes |
